Build on our Platform
to focus on Business
Comprehensive blockchain infrastructure
white-glove platform with rapid deployment,
enterprise compliance,
and best in class technical support
DeFi Price Feeds
Faster price feeds
Lower price
Reliable RPC for ecosystem
Uptime 10B+ req/month
Mean latency
High throughput
Peak throughput
Block time
Clients
From concept to 1’000’000 users
Key numbers
Complete platform, vertical stack
Enterprise layer
Compliance, Privacy, Identity — none of these is an issue on blockchain anymore. If anything, audits are much simpler and more efficient
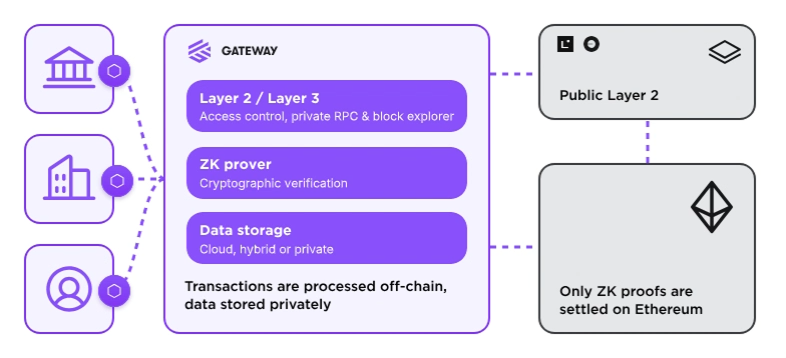
35+ Integrations
Deploy applications to your network in a matter of minutes: Indexer, Oracle, Swap, Account abstraction, Multisig and more. Choose Gateway native or 35+ partner integrations
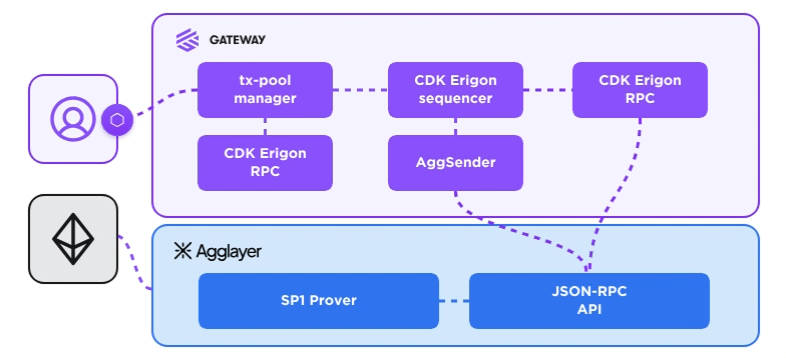
Core protocol stack
Whether you want to build a Layer 1 or Layer 2 solution, we’re here to help choosing the right stack for your solution, and orchestrating your chain
Servers
Solve your server needs with Gateway by utilising our globally distributed network of powerful machines. Choose Cloud, Hybrid or Secret Sequencer
This is what you can build

Fintech
Schedule a callOur fintech blueprint is ready to go live with your financial product in 4-6 weeks. Schedule a call to know more

Compliant De-Fi
Schedule a callLaunch a Real World Assets, or any other De-Fi project with compliance requirements in 1 month, scale it to millions of users

Supply chain
Schedule a callOur pre-compiled supply chain solution can be integrated into your enterprise in a matter of weeks

Gaming
Schedule a callPut your game on-chain for better traction and interoperability, mint unique objects - all ready to be deployed
We are Ethereum aligned
We work in close collaboration with Ethereum Foundation and Ethereum Enterprise Alliance to align on key Ethereum principles
Book a callOur partners
We guide you
every step of the way
Book a callDo it yourself
Deploy your chain in minutes, go live in a matter of days
Leverage our enterprise grade RPC for the needs of your project
Delegate your assets to the best in class validators
Select from a plethora of extra web3 services, ready to deploy
Mentions
Lumia
Pushing ZK to production — not just theory. From modular DA to decentralized sequencers, our work with @gateway_eth and @Agglayer is turning next-gen #RWA infra into reality. Shaping the foundations. 🤝
Haust
This journey wouldn’t have been possible without you. Thank you for powering our mission with trust, innovation, and unwavering support. Here’s to what we’ve built — and what we’re building next, together. @gateway_eth , you’re part of the Haust DNA.
CEO of Polygon
Watchout for @gateway_eth team! Beasts! 🫡🫡@mandrigin
Polygon
Exciting stuff! CDK-Erigon enables devs to build custom L2s with unmatched flexibility (35+ configs working with @gateway_eth) and high levels of zk performance (1K+ TPS). ⚡️ faster performance, greater scalability, improved upgradability for Prism Network
Celestia
Launching a rollup shouldn’t feel like rocket science. Viet(@braveryandglory) from @celestia shares how Gateway.fm lets you skip the complexity and go live in just a few clicks. Tap into Celestia’s DA, stay in control, and start building — faster.
Linea
Why do Linea projects choose Gateway? @DeclanFox14 from @LineaBuild shares how our platform as a service handles the heavy lifting—infra, ops, and more—so teams can focus on building and scaling.
Moonveil
I think Gateway is the one that we saw the strongest commitment, and also very strong fundamental tech understanding, and also the close co-building relationship with Polygon. Usually, we would prefer someone who is not only helping us to make the defer, but also why it's strategically meaningful to develop along this way, to guarantee the vision that we are trying to align with regarding our key partners.
Gnosis
... affordable and highly reliable RPC hosting services ... during the Chiado testnet merge, processing the first post-merge block. We look forward to this continued
24/7 Enterprise-Grade Support
Care, calmness, and reliability.
IT support across various time zones for your convenience, including alarms, rapid response time, and people on call. One team with Gateway.
Book a callStart building today
Are you impressed? Let's talk!
Our team of experts will help you design the optimal Shared prover solution for your needs
Supported proof systems
We support type 2 and type 1 zk proofs
Integration API details
Available in documentation and per request for enterprises
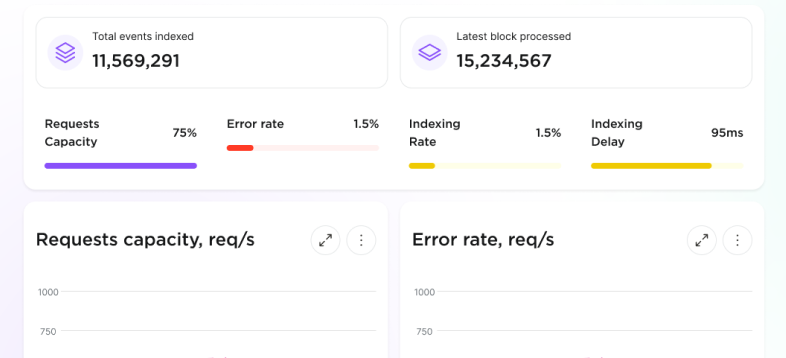
Monitoring capabilities
Catch an issue before it affects your network
Performance metrics
Dashboard with metrics and alerts coming soon
Schedule a technical consultation
Provide us your technical requirements to get the best advice on architecture. Or simply clarify details.

